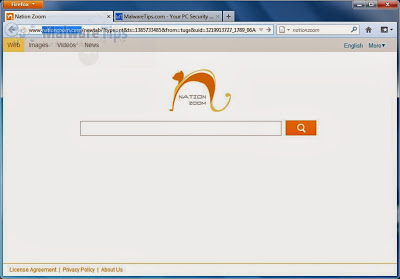
This in itself is not considered malicious as there are many legitimate programs that change these settings as well. What is considered malicious, though, is that it will also append the argument http://nationzoom.com to random Windows shortcuts on your desktop and your Windows Start Menu. When you launch Firefox, Chrome or Internet Explorer browser, the home page transforms itself into a Nation Zoom homepage, as illustrated below.
The Nation Zoom homepage will display advertisements and sponsored links in your search results, and may collect search terms from your search queries. The Nation Zoom hijack is used to boost advertising revenue, as in the use of blackhat SEO, to inflate a site’s page ranking in search results.
Nation Zoom is technically not a virus, but it does exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program.
Nation Zoom is an ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer (BHO) and Firefox/Chrome (plugin) and distributed through various monetization platforms during installation. The browser extension includes various features that will modify the default or custom settings of the browser including the home page, search settings and in some cases will modify Internet Explorer’s load time threshold, place a lock file within Firefox to prevent competing software from changing its settings as well as disable the browser’s Content Security Policy in order to allow for cross site scripting of the plugin.
Nation Zoom homepage did get on your computer after you installed a freeware software (video recording/streaming, download-managers or PDF creators) bundled with this browser hijacker.
For example, when you install VPlay, you will also agree to change your browser homepage to nationzoom.com and default search engine to search.yahoo.com.
However when you uninstall VPlay from your computer, your web browser’s default settings will not be restored. This means that you’ll have to remove Nation Zoom homepage from your favorite web browser manually.
You should always pay attention when installing software because often, a software installer includes optional installs, such as this Nation Zoom browser hijacker. Be very careful what you agree to install.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
Nation Zoom Homepage Removal
Please follow these steps in the correct order.
STEP 1: Uninstall Nation Zoom malicious programs from your computer
STEP 2: Remove Nation Zoom from Internet Explorer, Firefox and Chrome
STEP 3: Clean up the various Windows shortcuts that have been hijacked by Nation Zoom virus
STEP 4: Remove Nation Zoom virus with Malwarebytes Anti-Malware Free
STEP 1 : Uninstall Nation Zoom malicious programs from your computer
The Nation Zoom browser hijacker is usually installed with other malicious programs, which will either protect this infection from being removed from your computer or will display pop-up ads within the Web browser.
In this first step, we will try to identify and remove any malicious program that might be installed on your computer.
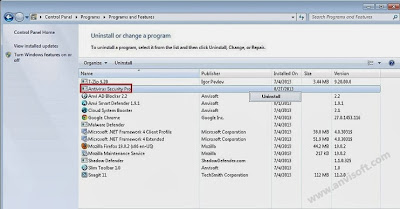
To uninstall the programs responsible for the Nation Zoom redirect, click the Start button, then select Control Panel, and click on Uninstall a program.
If you are using Windows 8, simply drag your mouse pointer to the right edge of the screen, select Search from the list and search for “control panel“. Or you can right-click on a bottom left hot corner (formerly known as the Start button) and select Control Panel from there, then select Uninstall a program.
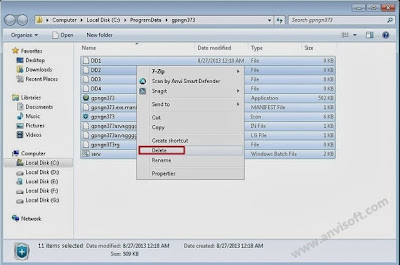
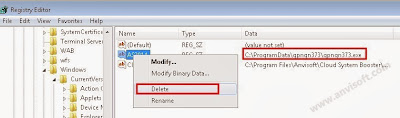
When the Add/Remove Programs or the Uninstall a Program screen is displayed, scroll through the list of currently installed programs and uninstall Wsys Control, Extended Protection, eSave Security Control, Desk 365, Nation Zoom browser protection and any other recently installed or unknown programs from your computer.
If you are having issues while trying to uninstall the Nation Zoom malicious programs, you can use Revo Uninstaller or IObit Uninstaller to completely remove this unwanted program from your machine.
Depending on what program has installed the Nation Zoom homepage, the above program may have a different name or not be installed on your computer. If you cannot find any unwanted or unknown programs on your machine, then you can proceed with the next step.
STEP 2 : Remove Nation Zoom from Internet Explorer, Firefox and Chrome
1. Remove Nation Zoom from Internet Explorer
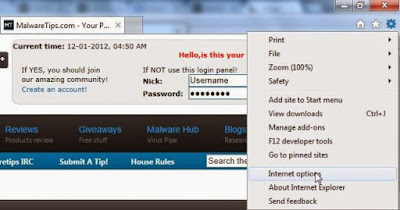
Open Internet Explorer, click on the gear icon (Tools for Windows XP users) at the top (far right), then click again on Internet Options.
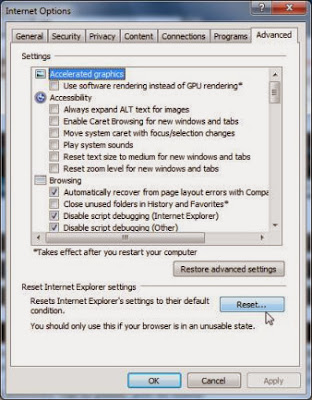
In the Internet Options dialog box, click on the Advanced tab, then click on the Reset button.
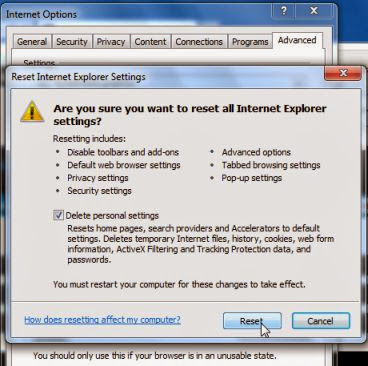
When Internet Explorer finishes resetting, click Close in the confirmation dialogue box and then click OK. Close and open Internet Explorer.
2. Remove Nation Zoom from Mozilla Firefox
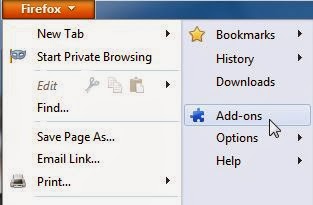
At the top of the Firefox window, click the orange Firefox button, then select Add-ons.
Select the Extensions tab, then remove Nation Zoom, Extended Protection and any other unknown extensions from Mozilla Firefox.
Reset your default search engine and homepage from NationZoom.com to their default.
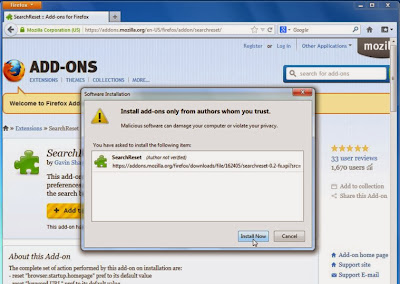
To reset your search engine and homepage to their default, we will use the SearchReset extension.This add-on is very simple: on installation, it backs up and then resets your search preferences and home page to their default values, and then uninstalls itself. This affects the search bar, URL bar searches, and the home page.
You can download SearchReset, and then we will just need to install it to revert Firefox to its default settings.
3. Remove Nation Zoom from Google Chrome
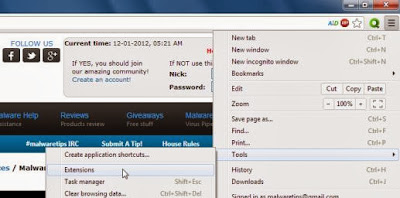
Click the Chrome menu button on the browser toolbar, select Tools and then click on Extensions.
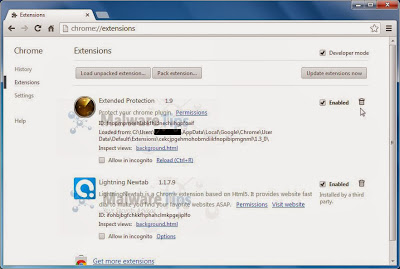
In the Extensions tab, remove Extended Protection 1.9, Lightning Newtab and any other unknown extensions by clicking the trash can icon.
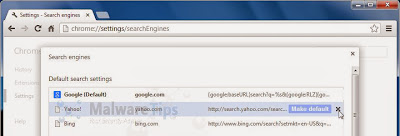
Set Google Chrome default search engine from Yahoo Search to Google.
Click the Chrome menu button, then select Settings and click on Manage search engines in the Search section.
In the Search Engines dialog that appears, select Google and click the Make Default button that appears in the row.
Search for Yahoo Search in the Search Engines list, and click the X button that appears at the end of the row.
Nation Zoom has modified your Google settings to open their webpage whenever you start your browser, so we will need to revert this change.
Click the Chrome menu button, then select Settings and click on One the New Tab page in the On Startup section.
STEP 3: Clean up the various Windows shortcuts that have been hijacked by Nation Zoom virus
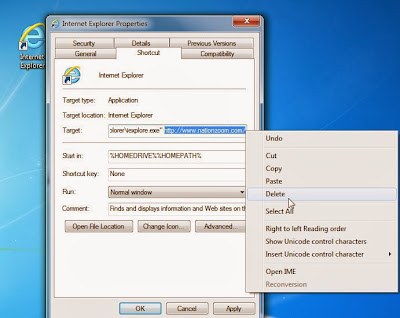
The Nation Zoom infection will hijack your browser shortcuts, so that each time you will click on the browser icon, you will be automatically be redirected to NationZoom.com. In this third step we will clean your browser shortcuts by removing the http://www.nationzoom.com argument from the Target field.
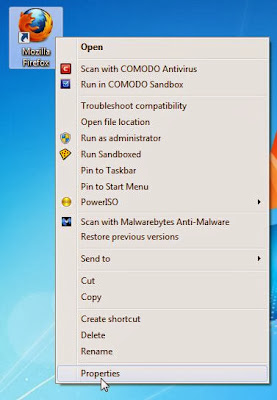
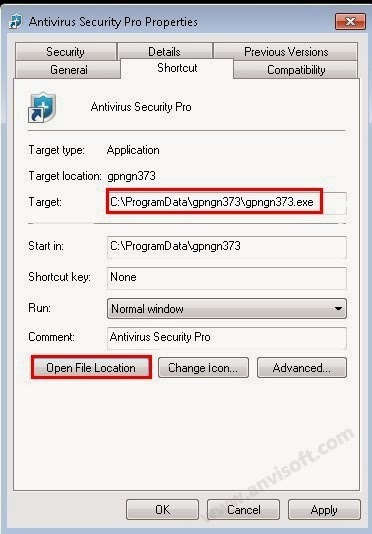
Search for your browser shortcut (Desktop, Taskbar or Start Menu Shortcut), then right-click on it and select Properties.
To view the Properties menu for the browser shortcuts pinned to your taskbar, right-click on the browser shortcut from the Taskbar, then right-click again on the browser icon as see in the below image.
In the Shortcut tab, in the Target field, remove the http://www.nationzoom.com.
These are the default shortcut path that should be in your Target box, if the Nation Zoom argument is in there, then you should remove it.
For Microsoft Internet Explorer: “C:\Program Files\Internet Explorer\iexplore.exe” for Windows 32-bit or “C:\Program Files\Internet Explorer (x86)\iexplore.exe” for Windows 64-bit.
For Mozilla Firefox: “C:\Program Files\Mozilla Firefox\firefox.exe” for Windows 32-bit or “C:\Program Files (x86)\Mozilla Firefox\firefox.exe” for Windows 64-bit.
For Google Chrome: “C:\Program Files\Google\Chrome\Application\chrome.exe”
STEP 4: Remove Nation Zoom virus from your computer with Malwarebytes Anti-Malware
Malwarebytes Anti-Malware Free utilizes Malwarebytes powerful technology to detect and remove all traces of malware including worms, trojans, rootkits, rogues, dialers, spyware and more.
Download Malwarebytes Anti-Malware Free, then double click on it to install the program. When the installation begins, keep following the prompts in order to continue with the setup process. Do not make any changes to default settings and when the program has finished installing, click on the Finish button.
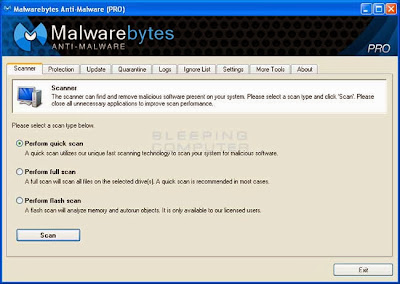
On the Scanner tab, select Perform full scan and then click on the Scan button to start scanning your computer.
When the Malwarebytes scan is completed, click on Show Results. You will now be presented with a screen showing you the malware infections that Malwarebytes Anti-Malware has detected. Make sure that everything is checked and click on the Remove Selected button.
In the Shortcut tab, in the Target field, remove the http://www.nationzoom.com.
These are the default shortcut path that should be in your Target box, if the Nation Zoom argument is in there, then you should remove it.
For Microsoft Internet Explorer: “C:\Program Files\Internet Explorer\iexplore.exe” for Windows 32-bit or “C:\Program Files\Internet Explorer (x86)\iexplore.exe” for Windows 64-bit.
For Mozilla Firefox: “C:\Program Files\Mozilla Firefox\firefox.exe” for Windows 32-bit or “C:\Program Files (x86)\Mozilla Firefox\firefox.exe” for Windows 64-bit.
For Google Chrome: “C:\Program Files\Google\Chrome\Application\chrome.exe”
STEP 4: Remove Nation Zoom virus from your computer with Malwarebytes Anti-Malware
Malwarebytes Anti-Malware Free utilizes Malwarebytes powerful technology to detect and remove all traces of malware including worms, trojans, rootkits, rogues, dialers, spyware and more.
Download Malwarebytes Anti-Malware Free, then double click on it to install the program. When the installation begins, keep following the prompts in order to continue with the setup process. Do not make any changes to default settings and when the program has finished installing, click on the Finish button.
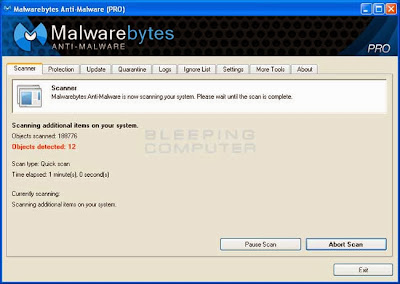
On the Scanner tab, select Perform full scan and then click on the Scan button to start scanning your computer.
When the Malwarebytes scan is completed, click on Show Results. You will now be presented with a screen showing you the malware infections that Malwarebytes Anti-Malware has detected. Make sure that everything is checked and click on the Remove Selected button.